Our panel of experts explain why your contact centre may need to improve its security, before sharing some advice for doing so.
Security Questions Are No Longer Enough
According to research, contact centre fraud rose by 113% in 2017, when compared to 2016. This is a sure-fire indication that fraudsters are getting smarter, so contact centres need to as well.
One technique of a smart fraudster is to identify organisations that still use old security techniques, such as asking security questions, and track social media and other sources of personal information to find out the answers.
Your responses to questions based on your first pet’s name, favourite movie or mother’s maiden name might be just lying there on your social media profiles.
These contact centres need to smarten up, so here are three quick tips for doing so.
1. Offer Two-Factor Authentication
This is a simple security precaution, but it is one that some organisations forget with continuous developments in technology.
Two-factor authentication makes use of technology that tracks when a customer logs into their account from a new device. This causes an alert within the contact centre system, which sends an immediate SMS to the customer, so they are aware that someone has logged into their account.
While the customer is likely the person that’s logging in, if they aren’t, they can then follow a link to reset their password and block the “foreign device”.

Two-factor authentication makes use of second method of authentication in addition to passwords.
Two-factor authentication makes use of second method of authentication in addition to passwords. It’s typically something you have (e.g. a mobile phone) or something you are (like a fingerprint).
When a customer does something that requires extra vigilance, such as logging in from a new device, this action then requires additional authentication such as entering a code sent to them via SMS.
2. Provide a Digital Security Key
A new application which is now being used by companies such as Google and Dropbox is to provide customers with a key that needs to be inserted into the user’s laptop/ computer USB port. Without the key, users cannot access their accounts.
As well as online security measures, having this extra physical precaution is great for those who are especially weary of protecting their accounts.
3. Training Advisors to Be Suspicious Also Has a Role
While it’s important to have technology in place, it is still important to educate advisors on the warning signs of how fraudsters may negotiate calls.
The team should learn this during initial training and this training must also be continuous, so that advisors can learn of new ways that fraudsters may try to navigate the contact centre’s defence.
Passive Voice Biometrics Is More Secure Than Active Voice Biometrics
In terms of fraudsters that attempt to scam your customers over the phone, voice biometrics seemed to have been the saviour, as the technology can detect whether or not the person calling the contact centre is who they say they are simply through the sound of their voice.
However, fraudsters had detected a sneaky way around this, as older voice biometrics systems ask customers to use a set phrase. Fraudsters would then phone their potential “target” and ask them a few questions to get a recording of their voice. With this recording, it may have been possible for customers to navigate the biometrics system.

Ashley Unitt
Fortunately though, passive voice biometrics prevents this from happening, as instead of asking for a set phrase at the start of the interaction, passive voice biometrics will monitor the customer’s voice throughout the conversation. While it’s relatively easy to record a set response, it’s practically impossible to record answers to the infinite number of questions the advisor may ask.
If the biometrics system detects a foreign voice, it will notify the advisor, while providing guidance or fraud protection actions.
Also, by removing this awkward first part of the conversation, where the customer has to authenticate their voice, you take away effort on the customer’s behalf, improving the service provided.
Thanks to Ashley Unitt at NewVoiceMedia
Advisors Could Be Bribed Into Sharing Sensitive Data
As the central warehouse facility for an organisation’s customer data, contact centres are often the weakest link in the security chain and the first point of attack for fraudsters – inside and out.
Advisors are sometimes bribed by criminals into passing along sensitive data, while less trustworthy individuals may voluntarily access customer records for their own gain.
Then there is the rising tide of social engineering where fraudsters claim to be a victim, reset a password on the victim’s account and then use that reset password to commit online fraud. All the while, scammers work in the background, using IVR to verify lists of compromised accounts that are purchased or sold on the dark web.
Scammers work in the background, using IVR to verify lists of compromised accounts that are purchased or sold on the dark web.
Thanks to technological advances, there are now smarter ways to carry out traditionally lengthy identification and verification (ID&V) checks to guarantee callers really are who they say they are.
Today’s cloud-contact centre technology allows DTMF (Dual-Tone Multi-Frequency) verification where customers are asked to key in account numbers and/or pin codes via an IVR system. Those numbers are checked against customer records which are then presented to an agent as and when required.

Colin Hay
However, we mustn’t forget our first line of defence. Back-up technology with a robust security awareness programme to keep your agents honest. You should also:
- Make sure advisors understand the latest trends in contact centre fraud and know how to spot the warning signs
- Develop consistent processes and communicate clear policies with a warning that transgressions are severely career limiting and liable to instant dismissal
- Do regular audits and consider introducing spot-checks to ensure staff are not inadvertently or deliberately copying customer data onto any personal device
Finally, make ‘customer information security’ an intrinsic part of your performance measurement criteria. If you look at agent interactions through customer security eyes, you’ll maintain your organisation’s corporate integrity and boost customer loyalty at the same time.
Thanks to Colin Hay at Puzzel
The Contact Centre Team Has Direct Access to More and More Information
Contact centres have always dealt with sensitive information. When agents acted as bridges between a voice and some corporate mainframe application there was minimal risk. However, increasingly interconnected contact centres increase the information risk substantially.
Calls are now being recorded, transcribed, analysed and reviewed. Agents are presented with contact histories and often have direct access to much more information than they have had in the past. Protecting information through access controls is a requirement.

Agents are presented with contact histories and often have direct access to much more information than they have had in the past.
The contact centre can benefit from both role and workflow-based access controls. Roles define what a person (agent, performance manager, or scheduler) can do. Workflow defines temporary access to information based on an assigned task. Agents should not routinely access call transcripts (it isn’t their role), but may need to when attached to an active training request (an assigned task).
Using these two approaches can provide a framework for thinking about information and who should access it and when. You will want to ensure that your vendors are able to enforce the rules that will keep your customers’ information safe and secure.
Establishing rules that are appropriate to your contact centre need not be complex but can be critical in preventing information breaches. The cost of these breaches can be very high, and that cost can be impacted by the rules (or lack thereof) that you have in place.
If you cannot prevent the breach entirely, you can show that best practices were followed and that you did your best to mitigate and limit the impact.
Bryant Eastman
If you cannot prevent the breach entirely, you can show that best practices were followed and that you did your best to mitigate and limit the impact. Doing nothing is no longer an option.
Your vendors should be just as concerned about information security as you are. Talk to them about how to leverage both role and workflow-based access controls to better protect your sensitive information.
Storing Customer Information Presents Risks
Industry-standard protections like role-based access controls are key to meeting even the most basic security best practices. However, having an assigned role is only as good as your ability to accurately know the user that is accessing the system – a process called authentication.
We constantly authenticate ourselves. This can be almost automatic in the case of human interactions (your face and voice) or more complex in the case of your phone (fingerprint or PIN). Computer systems typically use passwords that vary in the amount of complexity that they require and managing this complexity has been a topic of debate for almost as long as computers have existed.
Evidence shows that people are very, very bad at picking passwords. To “fix” this problem the password policy was invented. We all know about these – your password must contain a letter, a digit, upper-case, lower-case, and must be 20 characters long and change every five days.
Yet, research shows that in many cases these “strong” password policies actually weaken security, because a “strong” password is easy for the computer and very difficult for the human that has to remember it.

Bryant Eastman
Recent guidelines try to improve security by addressing human factors. For example, having passwords expire less often, reducing character restrictions, and increasing length makes it easier for people to choose passwords that are easy to remember and less prone to patterns to make them different each month.
Take an opportunity to evaluate the password policies for your contact centre. You may find that you can increase both security and user satisfaction at the same time – and that doesn’t happen very often!
Thanks to Bryant Eastman at NICE inContact
Cross-Channel Fraud Is Rising
Gartner recently predicted that by 2020, 75% of omnichannel customer-facing organisations will sustain a targeted, cross-channel fraud attack and the contact centre will be the primary point of compromise.
According to a Javelin Strategy & Research report, there were 16.7 million victims of identity fraud in 2017, hinting that fraudsters are evidently getting more sophisticated. It is therefore an crucial time for businesses to adopt an even more sophisticated approach to handle the risk and protect their customers.
To balance the customer experience with the need for security, many contact centres turn to voice biometrics, as it can play a key role within the contact centre and across multiple contact channels.
However, organisations can now go one step further, with the latest security systems offering a layered approach to security that can enable organisations to authenticate an individual and catch fraudsters based on HOW they talk, not just the sound of their voice.
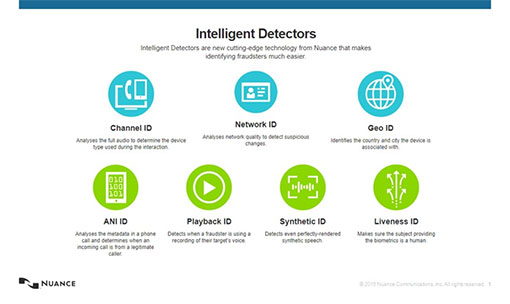
There are a number of intelligent detectors now being used to identify fraudsters

Sebastian Reeve
The technology enables frictionless and continuous authentication throughout the customer engagement, increasing customer satisfaction by reducing false rejection rate and also improving fraud detection rate.
Attacks need to be stopped in order to ensure contact centres compromised. This is why better security safeguards need to be implemented.
Thanks to Sebastian Reeve at Nuance Communications
Phone Payments Often Lack the Same Security as Online Payments
When customers make payments over the phone, they run a significant risk of divulging their sensitive and personal financial information without actually knowing what happens to it, how it is used and who has access to it.
It is therefore crucial for companies to equip their contact centres with secure payment systems that are GDPR-friendly and that will allow customers to connect in a direct and seamless way to the card payment network, in order to make payments while on calls.

Neil Hammerton
For instance, such payment systems should enable the customer to type in their credit card details directly through the phone keypad and share that information with the financial service provider directly, allowing for the advisor to be removed out of the equation altogether.
At the same time, it is crucial that while they make the payment, customers stay connected with the advisor through voice at all times to ensure they can flag any issues that arise and complete their payments securely and safely while staying on the call.
Thanks to Neil Hammerton at Natterbox
There May Be a Risk of Hackers Intercepting Calls
Any communication that involves personal or sensitive data, including voice calls, is ripe for exploitation, which is why such calls are subject to the strictures of the recently implemented GDPR legislation.
Unfortunately, many contact centres, including established financial services institutions, continue to rely on legacy telephony for internal collaboration and customer communication.
Legacy telephony typically lacks adequate security. By choosing headsets that support high-levels of encryption (between the device and the base unit), organisations can help guard against any risk of hackers intercepting calls.

Nigel Dunn
DECT standard security protects against wireless intrusion, but there are certain headsets that have features which go going beyond DECT Secure Level C, providing the very highest protection to users and customers alike.
If a customer is trusting the call centre agent with personal – and potentially sensitive – information, it is the contact centre’s responsibility to keep this safe. Therefore, using a headset which supports high-level encryption is paramount in the fight to safeguard customers’ information.
Thanks to Nigel Dunn at Jabra
Knowledge-Based Authentication Is No Longer Enough
For many organisations, security processes rely on some form of knowledge-based authentication that uses shared questions. Apart from the fact that these processes take a significant amount of time to complete, they are also no longer a secure method of verifying someone’s identity.

Efrat Kanner-Nissimov
With heightened sensitivity around issues of online security and fraud, organisations need to prioritise processes that enable seamless and effective security and customer experiences.
For example, with real-time authentication (RTA), a caller’s identity can be verified within the first few seconds of a natural conversation. This means that the agents are notified in real time if they are speaking with the right person based on their voice alone, eliminating any opportunity for fraudsters without inconveniencing the customer.
Thanks to Efrat Kanner-Nissimov at NICE
For more from our panel of experts, read our articles:
- 10 Techniques to Reduce Time Spent on ID and Verification
- How Do I Integrate Contact Centre Technology With My CRM System?
- The Top 10 Emerging Technologies in Contact Centres
Author: Charlie Mitchell
Published On: 14th Jan 2019 - Last modified: 29th May 2024
Read more about - Technology, Biometrics, Colin Hay, Jabra, Natterbox, NICE, NICE CXone, Nuance, Puzzel, Security, Vonage